Verifying customer identity is vital to safe business operations. Businesses obtain customer information and ratify it through a process called Know Your Customer (KYC), which begins with a Customer Identification Program (CIP). FinCEN’s Final Rule sets out the CIP requirements, answering many questions such as “What is CIP?”.
This guide determines what a CIP is and how it relates to the broader KYC process, expanding on the nuances and specificities of Customer Identification Programs between institutions and industries.
What is a Customer Identification Program?
When regulated businesses establish new relationships with users, they must verify the customer’s identity. While this is particularly pertinent for financial services, its importance also extends to other industries. This trend is expected to continue into 2024 and beyond.
A Customer Identification Program is a procedure that most companies must follow when onboarding new clients. It is designed to deter bad actors, financial criminals, and known or suspected terrorists. It proves that customers are who they say they are and is a crucial first step in the KYC process.
The Financial Crimes Enforcement Network’s (FinCEN’s) Final Rule mandates that a company’s CIP must be ‘appropriate to its business size.’ This means every company must analyze customer details until there is a ‘reasonable belief’ that the customer is indeed who they say they are. This regulation provides companies with a degree of autonomy and flexibility when deciding and enacting their program.
CIP vs KYC: What’s the difference?
The critical difference between a Customer Identification Program and a Know Your Customer strategy is that a CIP is a component of KYC:
-
Customer Identification Program (CIP): FinCEN and the USA Patriot Act require a financial institution to form a reasonable belief that it knows the identity of its customers.
-
Customer Due Diligence (CDD): The due diligence process fosters a risk profile for each customer that compliance and KYC officers can use to make informed user decisions.
-
Ongoing Monitoring: The due diligence process is performed on an ongoing (continuous) basis. This gives institutions real-time information so they are fully informed of their users.
For more information on KYC Verification, read KYC Verification in 3 Steps.

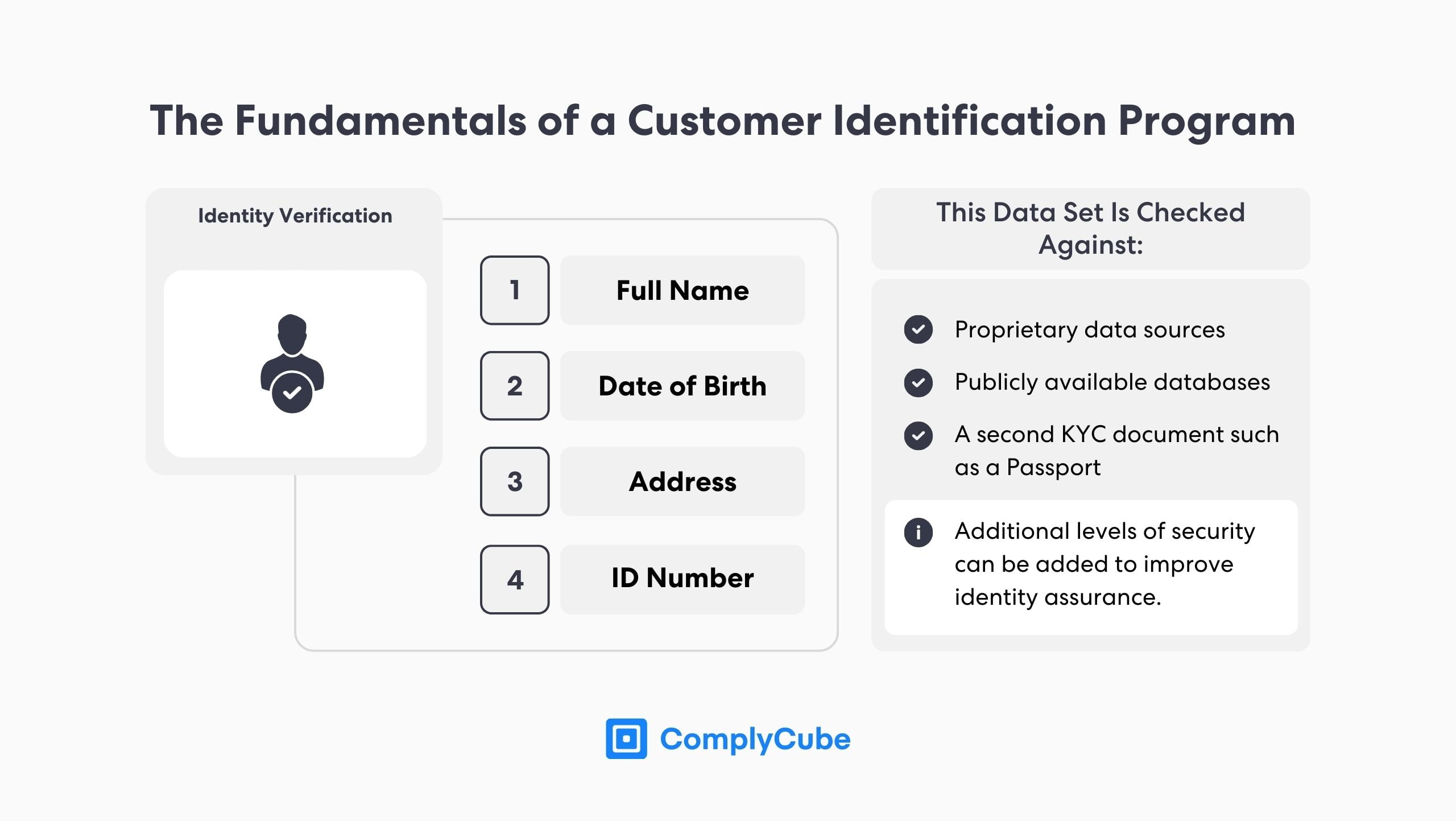
What Information Must a CIP Extract?
There are 4 essential requirements that must be obtained when an institution begins a CIP. They are:
-
Full Name
-
Date of Birth
-
Address
-
ID Number
The data extracted is verified against the documents supplied by the potential customer and third-party trusted databases. In this way, the business can paint a clear picture of who the user is so it can decide whether the individual can gain access or continue to use the service. Companies can add additional layers of identity verification to increase security as dictated by the company’s Risk Base Approach (RBA) or regulatory bodies.
When requesting information from an old or new account, such as a proof of address, an institution must provide adequate notice for the data or documents to be provided; this is mandated in the Final Rule.
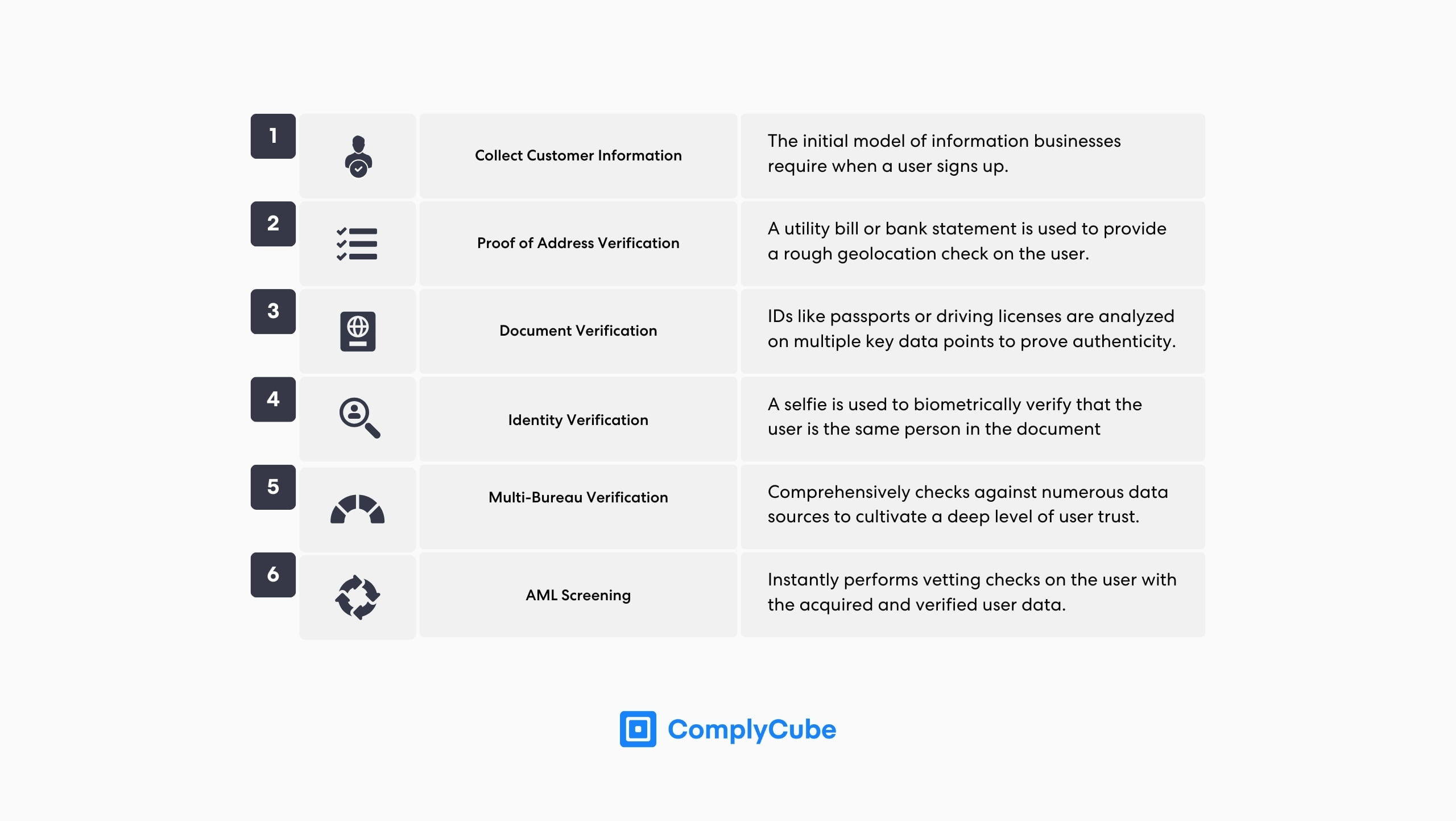
CIP Requirements for Financial Institutions
While the Final Rule is left open to each company’s discretion, there is generally an aggregated framework for the process.
The first step in the process is collecting customer information; this is crucial as it lays the groundwork for identifying the individual’s true identity. This preliminary stage gives the company something to measure the user’s documents against when they upload their ID.
Verifying user documents such as a passport, driver’s license, or any other government-issued ID is essential. This helps the company corroborate the information provided initially: Name, Date of Birth, Address, and ID number (such as a taxpayer identification number or social security number in the US).
Companies then ratify this information against a trusted third-party database, such as a credit bureau, postal service, or other financial institution. Depending on the company’s risk tolerance, proof of address may be requested as an additional layer of identity assurance. This typically comes in the form of a utility bill or bank statement.
Once a business is content with the level of identity assurance, it runs an AML screening. This verifies that the user is not involved in illegal activities and helps the government fight against financial crime. Leading KYC/AML solutions provide multiple AML screening services including, but not limited to, Sanctions & PEP Screening, Adverse Media Checks, and Watchlist Screening.
Identity Verification (IDV) Procedures
Once user information has been acquired, their true identity must be verified. This can be done in several ways, depending on industry-specific regulations as well as a company’s corporate risk-based approach. KYC services provide a host of solutions that are indispensable in extracting reliable customer data and innovating customer onboarding processes. The solutions can be customized and tailored to fit the needs and operations of a business.
Proof of Address (PoA) Check
Checks for Proof of Address leverage state-of-the-art OCR and decision-making engines to extract relevant information from Proof of Address documents in seconds. These documents include bank statements, utility bills, driving licenses, and tax documents that are checked for 2 criteria:
-
Data on the PoA document is matched against the details provided by the client upon registration.
-
The geolocation of the provided document is tested for proximity to the IP address of the upload.
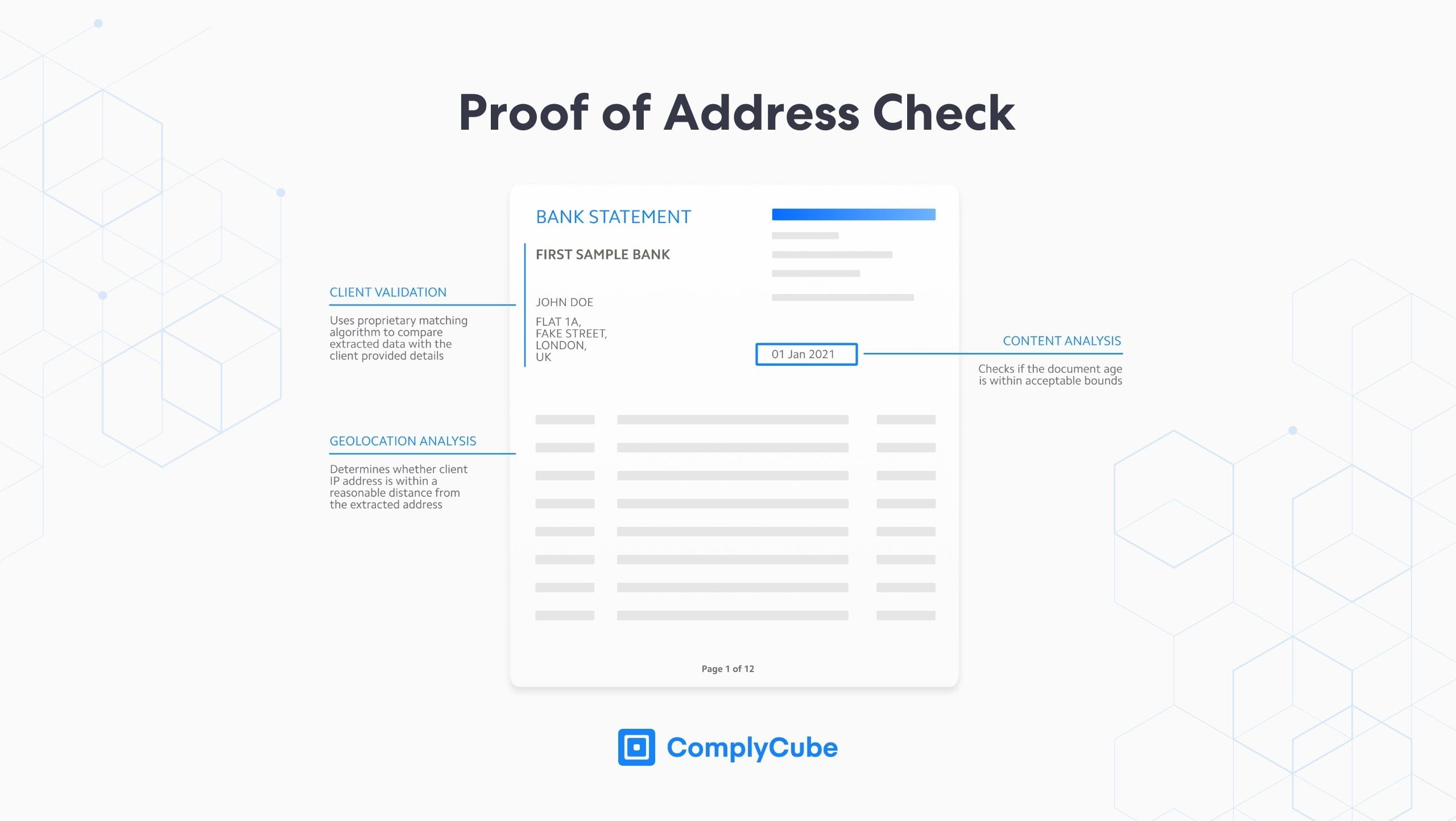
PoA verification takes less than 15 seconds to complete on average, making it a seamless yet reliable method to strengthen customer authenticity. Discover more about PoA Verification here: A Robust Guide to Proof of Address Checks (PoA).
Document Verification
Document verification can, in some circumstances, pertain to the remit of PoA. However, where high levels of identity assurance are required, such as financial services, other identifying documents, including a passport, are required.
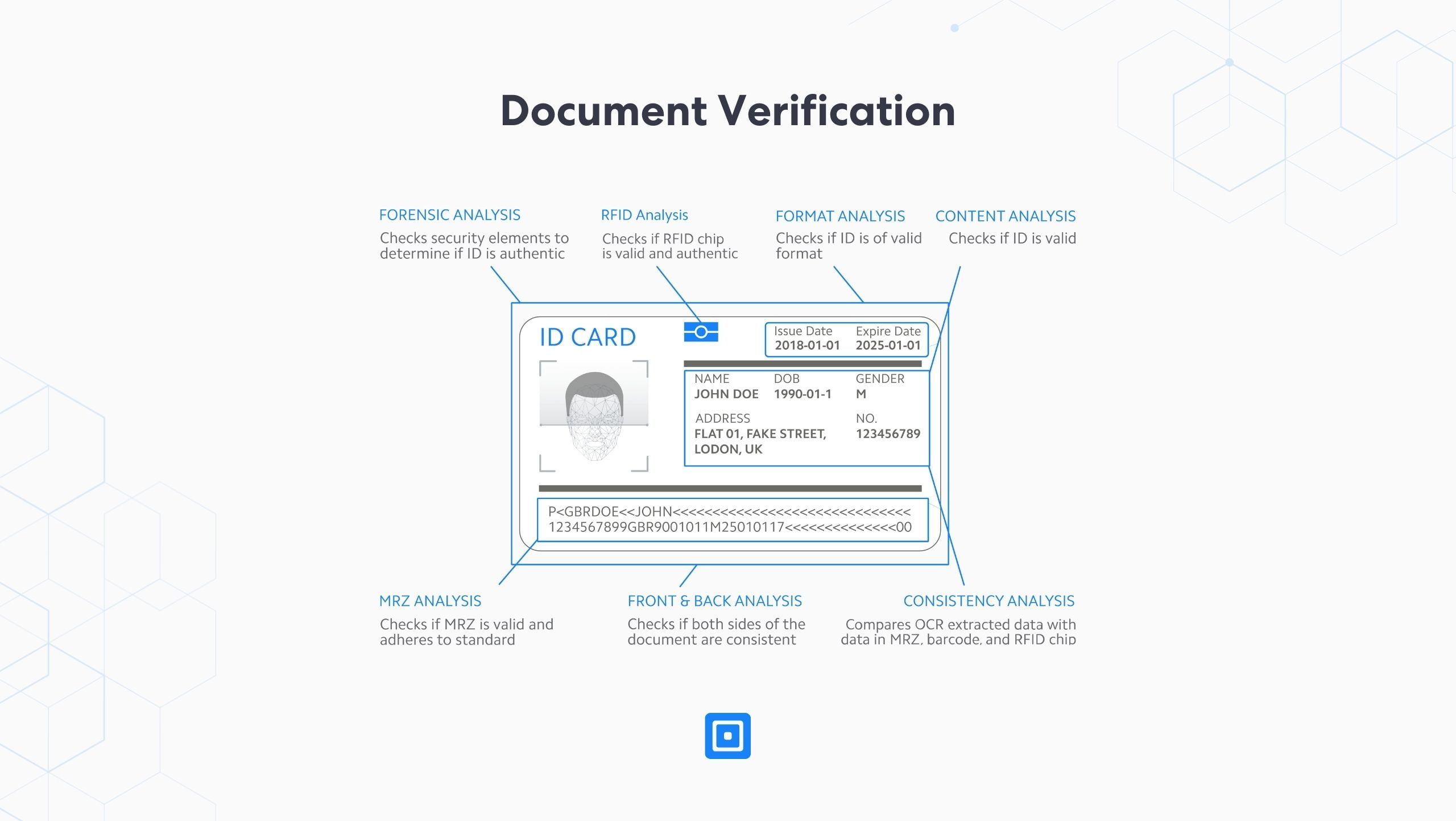
Using bespoke AI-powered analytics technologies, these checks can analyze multiple integral data points instantly, including:
-
Forensic Analysis
-
RFID Analysis
-
Format Analysis
-
Content Analysis
-
MRZ Analysis
-
Front & Back Analysis
-
Consistency Analysis
These checks auto-redact any sensitive information, such as images on minors’ passports, MRZ codes, and more, ensuring both the service provider and the business adhere to all jurisdictional data privacy laws.
For more information on the nuances of a document verification process, read: What is Document Verification? An In-Depth Look at ID Verification.
Biometric Verification
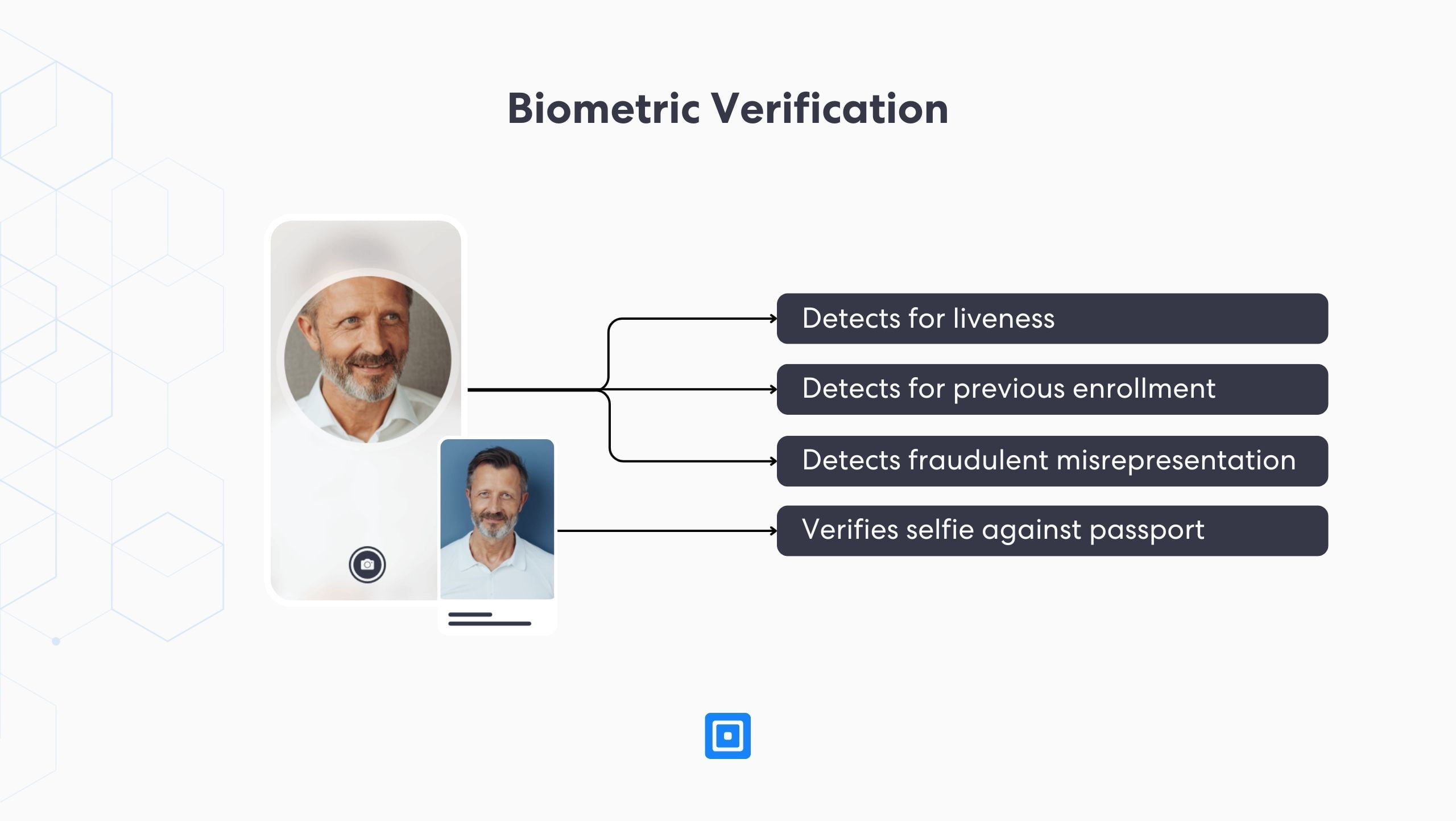
Biometric verification is the final piece of the identity assurance puzzle and is swiftly becoming a modern CIP requirement. Once completed, financial institutions should have sufficient confidence that the user is who they say they are, and an account can be opened.
This process matches a live selfie against the image in the ID document. Leveraging machine learning technologies, biometric verification detects the liveness of a selfie via certain innovative and advanced technologies, including Presentation Attack Detection (PAD).
PAD technology constructs 3D facial maps, conducts detailed analyses of skin texture and micro-expressions, identifies pixel tampering, and recognizes various disguises, including masks. This ground-breaking technology instantly detects any fraudulent attempts with precision at a speed that would be impossible for a human to mimic.
This accuracy at such a vast scale mitigates the number of false positives and increases the volume at which companies can onboard new clients. Learn more about Presentation Attack Detection here: ComplyCube Bolsters ID Verification with Liveness Layer.
Multi-Bureau Check
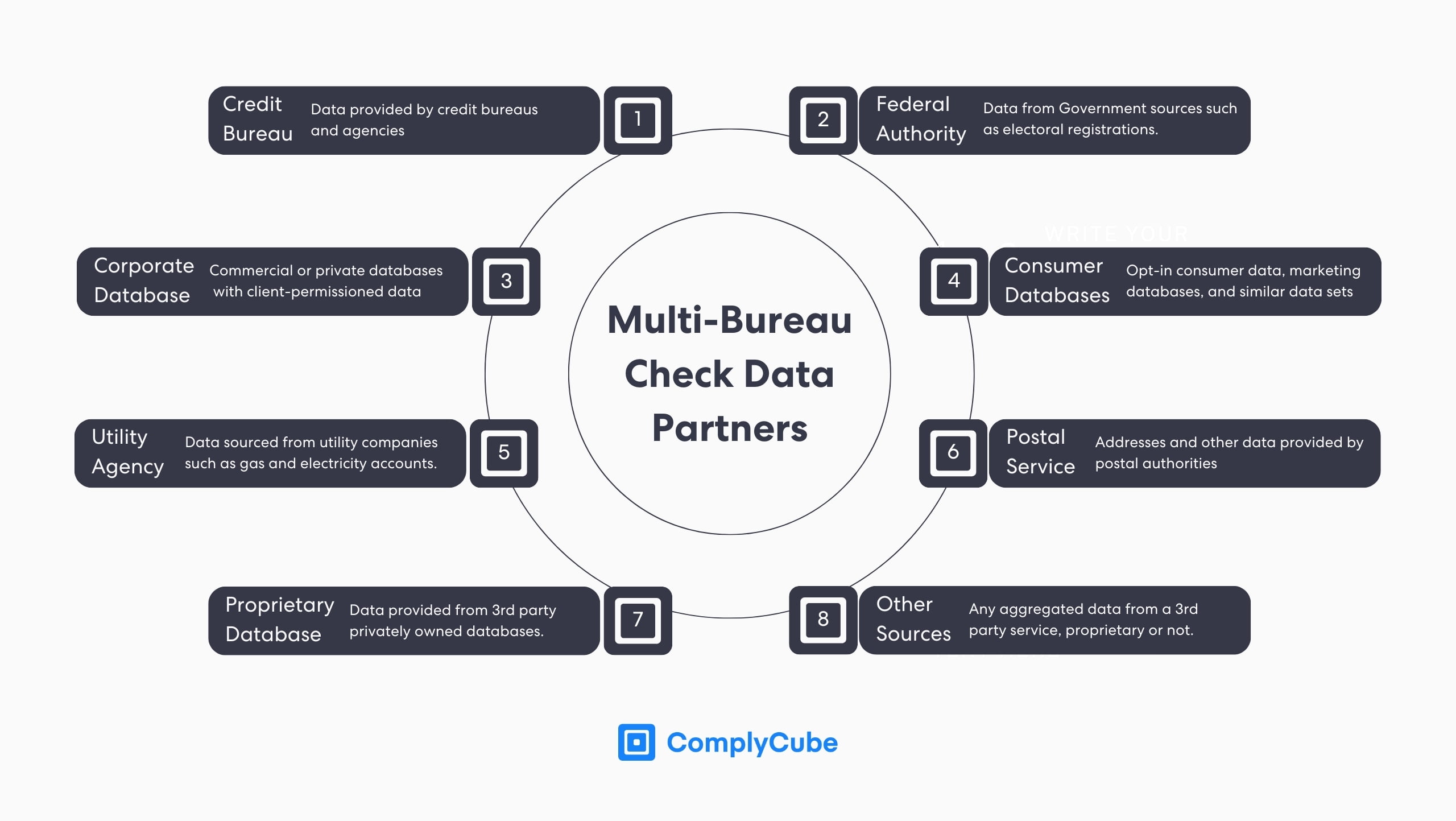
A Multi-Bureau Check offers a comprehensive layer of financial and informational background verification, cultivating deeper trust between the user and the service. Multi-bureau verification synchronously examines various bureaus and databases, such as credit unions, thereby performing a multifaceted vetting of a user’s background.
This method is usually used to amplify an existing level of identity assurance. For example, if a user were to apply for a loan after having opened an account with a bank. Typical partner databases can be viewed below.
Which Institutions are Bound by the CIP Rule?
FinCEN’s CIP requirements and Final Rule were created for financial institutions; however, they have become the global standard or expectation for all industries requiring the administration of a Know Your Customer process. For this reason, the CIP rule makes a good point of reference for any institution that needs to verify the identity of its customers.
The digitalization of the global economy has spurred economic growth by connecting individuals from all over the world. However, trust in identity is crucial for a fully digitalized and global economy to flourish.
This is why FinCEN’s First Rule can be applied to more businesses than just financial institutions. It’s already been established that the CIP rule must be proportionate to a business’ size and should be dictated by an industry’s identity assurance regulation and a company’s risk-based approach.
Some industries are not legally required to enact a KYC process and, therefore, a Customer Identification Program; however, online sectors with less regulation might choose to do so based on that company’s corporate risk tolerance.
How a Thorough CIP Helps Prevent Money Laundering
A Customer Identification Program is instrumental in helping financial institutions curb money laundering activities. Federal law requires these programs to collect a customer’s identifying information, including full name, identification number, date of birth, and address. This foundational step is critical in preventing money laundering and other financial crimes.
A CIP is far greater than simply retrieving customer data accurately; it is the beginning of an investigation into the authenticity of each piece of information. This information is continuously monitored to ensure the user’s circumstances do not change.
There is every possibility that a user’s situation, and therefore associated risk, will evolve throughout their relationship with a business. For example, a customer might open a bank account with no initial political connections but, over time, could develop associations with influential political figures.
Financial institutions can form a sufficient belief in their customers’ identities and act accordingly by adhering to the stringent measures discussed in this guide, coupled with a detailed broader KYC strategy.
A report on money laundering in the British property industry found an increasing need for technology-assisted Identity Verification and that more traditional methods were quickly becoming outdated.
These methods [manual KYC and AML checks] alone are no longer enough.
This represents a shifting landscape across a wide array of industries, where AI and machine-powered IDV solutions will become common practice across multiple industries. Money laundering in the real estate industry is nothing new, but reports show the increasing aptitude of the UK, particularly London, for real estate money laundering activities. This is, however, an escalating issue across multiple industries over the globe.
A thorough investigation of a client’s identifying details is essential, as it allows businesses to comply with regulatory policies and fortifies the financial system against the perils of illicit activities. This ensures that each account opened is based on a foundation of trust and verified identity.
CIP for Customers vs Businesses
The Customer Identification Program rule establishes a consensus for a robust Customer Identification Program, and the same framework can be applied to institutions embarking on new relationships with other businesses. This process is generally called Know Your Business (KYB), but a similar CIP process is required for any new partnership agreement.
An equivalent data set is required, including the Business name, registration address, incorporation date, and government-issued business license or employer identification number. However, the crucial difference, or addition, is determining the ultimate beneficial owners of the business.
This process can be incredibly challenging as business layers, owners, and proprietors can be masked by natural circumstances or deliberately through several layers. Generally, business owners are intentionally masked because there is something to hide from government and regulatory bodies. This further denotes the significance of these measures and why a thorough due diligence process is key to determining the real owners and operators of the business and their backgrounds and motivations.

Choosing a CIP and KYC Verification Service
Refining a Customer Identification Program (CIP) as part of a wider KYC (Know Your Customer) strategy is vital for businesses aiming to comply with Anti Money Laundering regulations and prevent fraud. This requires meticulous attention to detail and a deep understanding of regulatory requirements and customer profiles.
ComplyCube’s solutions include an all-in-one, user-friendly portal that is swiftly becoming an essential tool for compliance officers. This platform features advanced automation toggles and fast-fail thresholds, which streamline the client acquisition process and refine internal operations with efficiency-enhancing tools.
Automated KYC solutions alleviate businesses from the stress of monitoring shifting regulatory landscapes while providing seamless user experiences. A strong CIP and KYC service will do this without forsaking the integrity and security of the extracted data. ComplyCube’s AI-powered KYC services could help relieve your business’s trepidations over regulatory compliance. If this is a subject of concern, get in touch below.