Presentation Attack Detection (PAD) is a key component of a robust biometric verification process. PAD helps fortify identity verification by detecting Presentation Attacks (PAs) and fraudulent attempts to gain unauthorized access. With advanced AI-powered deepfake attacks on the rise, PAD solutions have become critical for organisations to safeguard their stakeholders, and their reputation.
This guide explores different kinds of presentation attacks, and the need for implementing presentation attack detection solutions.
What is Presentation Attack Detection?
PAD works by distinguishing between authentic biometric samples, such as a live person’s face or fingerprint, and presentation attack instruments like printed photos, fake fingerprints, latex masks, or digital images. Advanced PAD technologies, such as liveness detection, are adopted to enhance security in biometric authentication processes, which are widely used by financial institutions, law enforcement agencies, and many more organizations.
The case for implementing PAD continues to crystallize, as recent research finds that 90% of all document-based fraudulent practices are driven by presentation fraud. The use of deepfakes, which increased by 704% in the US in the second half of 2023 alone, points to a critical point in the discussion: presentation attacks are becoming increasingly sophisticated.
Presentation Attack Detection and Biometric Verification
Even though facial recognition technology has massively improved worldwide security, it’s important to remember that biometric authentication isn’t infallible. Presentation attacks can subvert identity authentication processes by using deceptive techniques and discerning presentation attack instruments.
Implementing PAD allows organizations to distinguish real users from fraudsters using biometric identity verification. Biometric data is taken from provided images, documents, and videos and analyzed by advanced AI-powered technology that can then draw precise conclusions by examining microexpressions, skin texture, and more.
Types of Presentation Attacks
Fraudsters use several methods to deceive facial recognition technology, including printed photo attacks, video replay attacks, and 3D masks.
Printed Photo Presentation Attack

Print attacks are one of the simplest forms of presentation attacks. Without PAD technology present, attackers can easily bypass facial recognition authentication processes by presenting printed identity documents or images of another person.
These photos are often taken from social networks or even the dark web. Unauthorized users gain access by subverting these facial biometric systems, committing identity fraud due to the lack of face presentation attack detection.
Occasionally, printed photos are used as masks in these attacks. Fraudsters will create a mask from a printed photo by cutting out eye holes to blink and bypass liveness detection.
Governments and financial institutions are often the primary targets for presentation attacks using printed photos, as their biometric systems protect large volumes of high-value assets and information.
However, it’s important to remember that anyone can be a target of these attacks:
As of 2023, 40% of businesses in the US were vulnerable to presentation attacks, with only 60% of organizations implementing the necessary PAD measures using biometric authentication processes.
Replay Attempts and Deepfake Attacks
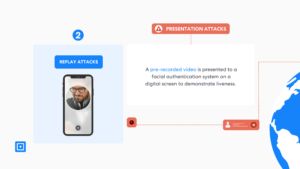
In replay attacks, the attacker plays a pre-recorded video or presents a digital image to the facial authentication system on a screen. This attack can mimic the natural movements and characteristics of a person’s face very well, as videos can capture blinking and subtle eye movements to appear like a live person.
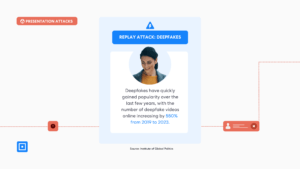
Deepfakes, a sophisticated form of synthetic media used in presentation attacks, are also a form of replay attacks. They consist of artificial photos or videos created by advanced machine learning called “deep learning”. Deep learning differs from standard machine learning because it operates with a special class of algorithms called a neural network, which aims to replicate how our brain retains information. “Hidden layers” of nodes are utilized within the network, which perform mathematical transformations to convert input signals into output signals. In the context of deepfakes, it converts authentic images into realistic fake images, offering scammers a great way of deceiving authentication systems.
Deepfakes have quickly gained popularity over the last few years, with the number of deepfake videos online increasing by 550% from 2019 to 2023.
Identifying a presentation attack that utilizes deepfakes requires advanced PAD methods to spot subtle inconsistencies such as unusual blinking patterns or digital artifacts.
The Institute of Global Politics recently interviewed the journalist Emanuel Maiberg on the rise of deep fakes, and stated the following in the article:
“Recent advancements in generative AI have made everything even easier and more realistic, with Stable Diffusion technology and other text-to-image AI tools, you can take photos of someone and create a custom AI model of the person’s identity.”
3D Mask Presentation Attack
Presentation attack methods also include 3D mask attacks, in which fraudsters present a 3D mask with their target’s physical characteristics to deceive biometric systems that use facial recognition technology. These masks are often made using a mold of their target’s face to replicate the facial biometric characteristics of the genuine user with high precision.
The Case for Presentation Attack Detection
Presentation attack detection is critical for fraud prevention and provides organizations with the necessary security to avoid financial losses and data leaks.
Statistical Overview
The need for presentation attack detection software is more than apparent when we look at the financial cost of online fraud and the wide reach of fraudulent practices:
Recent research found that presentation attacks account for 90% of all document-based fraudulent attacks, underlining the need for a robust biometric PAD process.
Deepfake attacks and other advanced forms of presentation attacks that can subvert facial identity verification systems saw a real increase. In just 2023, the use of deepfakes to deceive facial identity checks rose by 704% in the US.
The Federal Trade Commission stated that American consumers lost over $10 billion in fraud in 2023, which includes various forms of identity theft facilitated by inadequate identity verification measures.
Compliance and Best PAD Practices
The framework for evaluating presentation attacks is developed within ISO/IEC 30107-3:2017.
Compliance with ISO 30107 helps ensure that biometric systems can accurately distinguish between genuine biometric traits and fake or altered ones.
Official websites and linked source publications provide guidelines for best practices in presentation attack detection.
Introducing a Biometric PAD System for Identity Verification
Using liveness detection to spot deepfakes, printed photos, or other PAD instruments is critical to a strong IDV and KYC solution for any business.
Liveness Detection
A liveness detection solution ensures that your customer or user is physically present and alive during the authentication process, eliminating the possibility of deepfake, replayed video, or spoofed images gaining unauthorized access.
Advanced presentation attack detection software should include precise liveness detection to authenticate users. To prevent presentation attacks, these liveness detection solutions should also be able to analyze subtle micro-expressions and facial textures to recognize pixel tampering or any kind of mask.
For example, liveness detection will monitor that a person transferring money is present during the transaction, ensuring they are not being impersonated.
Example Industry Applications
Financial Services: Protects against fraudulent transactions and account takeovers by ensuring that only real, verified users who are physically present can access sensitive information.
Healthcare: Secures patient data and correctly identifies individuals accessing medical records.
Border Control: Enhances border security by accurately verifying travelers’ identities and detecting fraudulent documents.
Presentation Attack Detection with ComplyCube
We offer a market-leading PAD solution, which uses an AI-powered liveness detection check to examine precise facial features.
ComplyCube’s Identity Verification Solutions for PAD
At ComplyCube, we utilize a PAD Level 2 ISO-certified biometric AI engine for presentation attack detection by verifying liveness through contrasting facial similarity data points between the submitted video and an image from a government-issued document. In addition, we use 3D face mapping to check if a user has enrolled before under different details.
Contact our team of KYC specialists to learn more about how presentation attack detection can fortify your authentication processes and safeguard your organisation.