Real World Asset tokenization (RWA tokenization) is the transition of ownership rights onto the blockchain. A security Token Offering (STO) is when a company distributes tokens that represent digital ownership of a particular asset, typically equity. However, various RWA rules and regulations, as well as emerging Know Your Customer (KYC) STO compliance requirements, must be met.
This guide digests the new regulations impacting digital securities and explains how Security Token Offerings are anticipated to revolutionize the global financial markets.
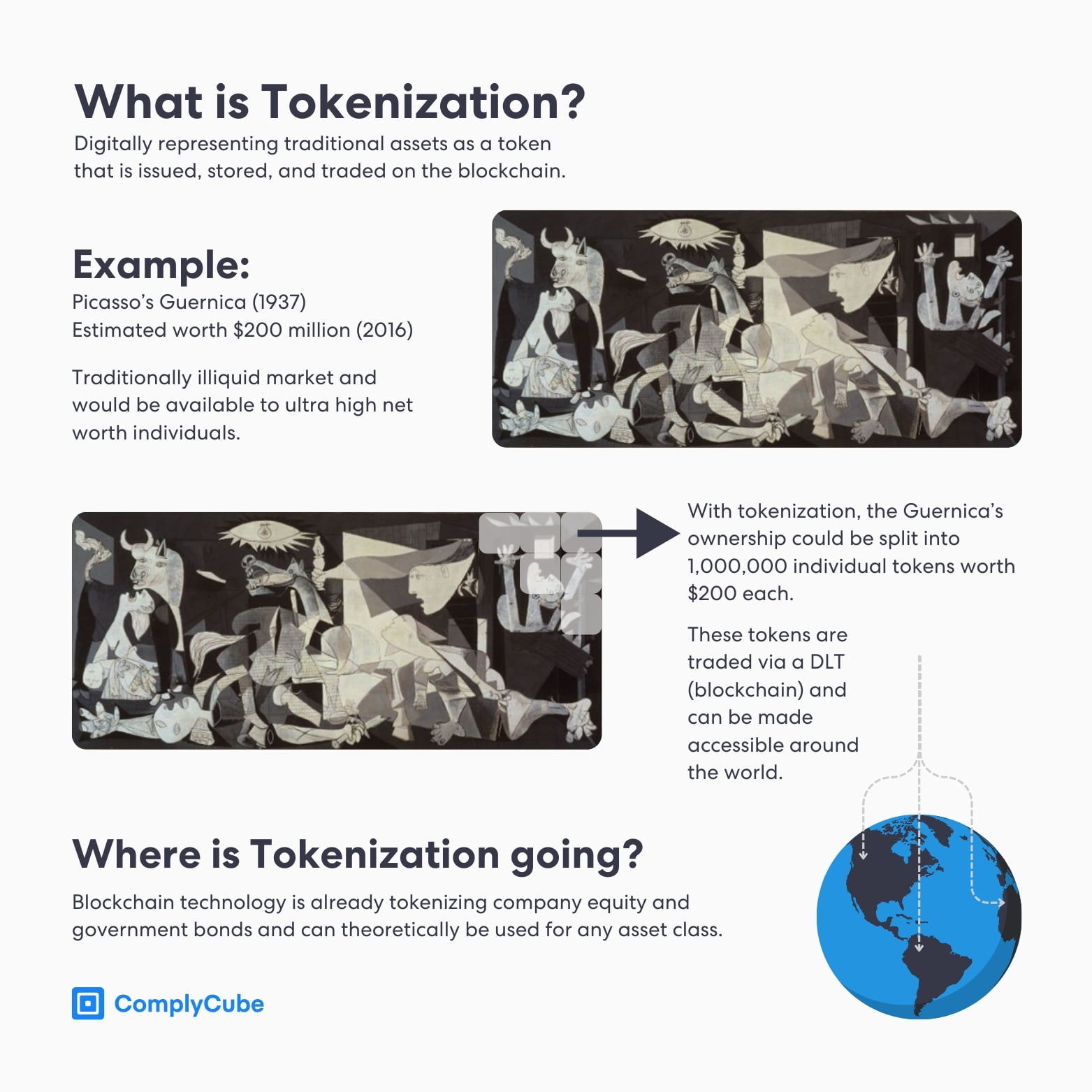
What are Digital Securities?
Digital securities are virtual representations of ownership stored on the blockchain; they act as a digitally owned replica of traditional security, such as company equity. However, any asset, ranging from real estate to art, can theoretically be tokenized on-chain.
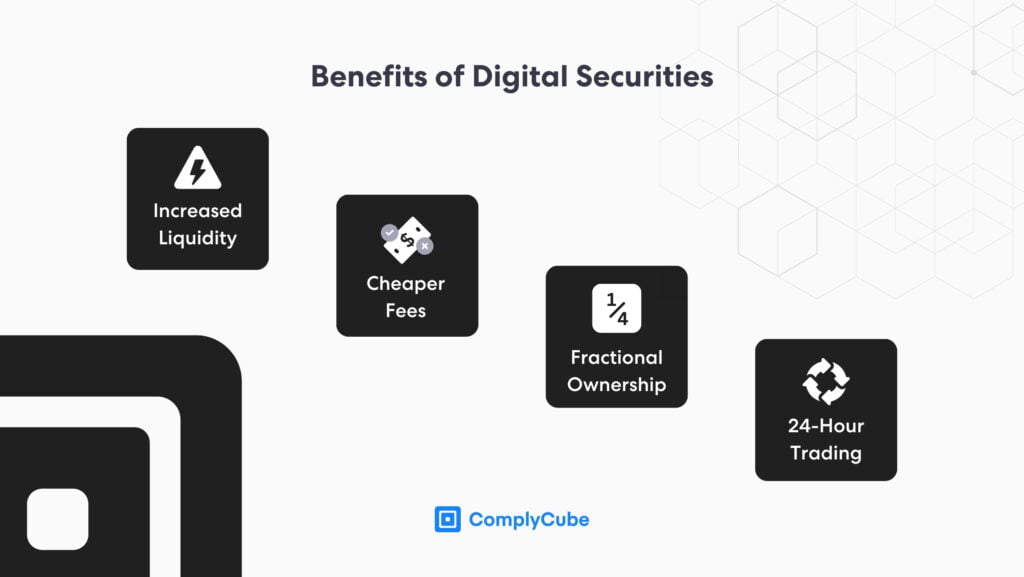
Trading security tokens that represent a traditional financial asset, such as tokenized company stock, offers various perks for users and traders:
- Increased liquidity
- Reduced costs of trading
- Fractional ownership
- 24-hour trading
Digitizing securities would also democratize global capital markets, the vast majority of which are currently unavailable to retail investors. The retail investor market is also a growing one. Following the 2007/8 financial crisis, global retail investor levels dropped for obvious reasons. However, there has been a significant bounce back over the past decade, and retail investors display a growing appetite for their own financial welfare.
Digital securities not only offer increased exposure to current financial market participants but also act as an incentive to those who are not. Therefore, they act as a vehicle for achieving greater financial inclusion around the world.
A significant feature of the cryptocurrency market is its ability to buy and sell digital assets 24/7. This innovation was driven by smart contracts’ functionality; smart contracts can verify a contract (such as the transfer of funds) without an intermediary, permitting trading at any time of the day.
Because of this, Centralized Exchanges (CEXs), such as Coinbase, also allow trading around the clock. This trading, however, is not facilitated by a smart contract. The CEX itself acts as the intermediary, creating a similar user experience to traditional trading platforms.
As the entire crypto market is tradable 24/7, the New York Stock Exchange opened discussions around opening a 24/7 stock market which would likely streamline the transition towards a digitized and tokenized financial market.
What is a Security Token Offering?
An STO is the distribution of company assets on the blockchain. These assets are tokenized, meaning they exist on the blockchain and act as a digital representation of ownership. The digital tokens distributed in this event are considered securities by law and, therefore, must adhere to regulations and policies enacted by leading securities regulators, such as:
- The Securities and Exchange Commission (SEC, America)
- The Securities and Futures Commission (SFC, Hong Kong)
- Financial Conduct Authority (FCA, United Kingdom)
STOs are gaining increasing popularity as a method for corporate fundraising and are starting to be used instead of Initial Public Offerings (IPOs). An STO must comply with the security legislation in the location where the digital security token is being transacted. Such regulations typically include disclosure, transparency, and user protection.
STO vs ICO
An STO is an initiative for raising capital or publicly distributing financial instruments on the blockchain, such as company equity. Initial Coin Offerings (ICOs) raise funds through the selling of utility tokens, which grant access to a business’s platform or services. The utility token ultimately acts as the engine behind a company’s project.
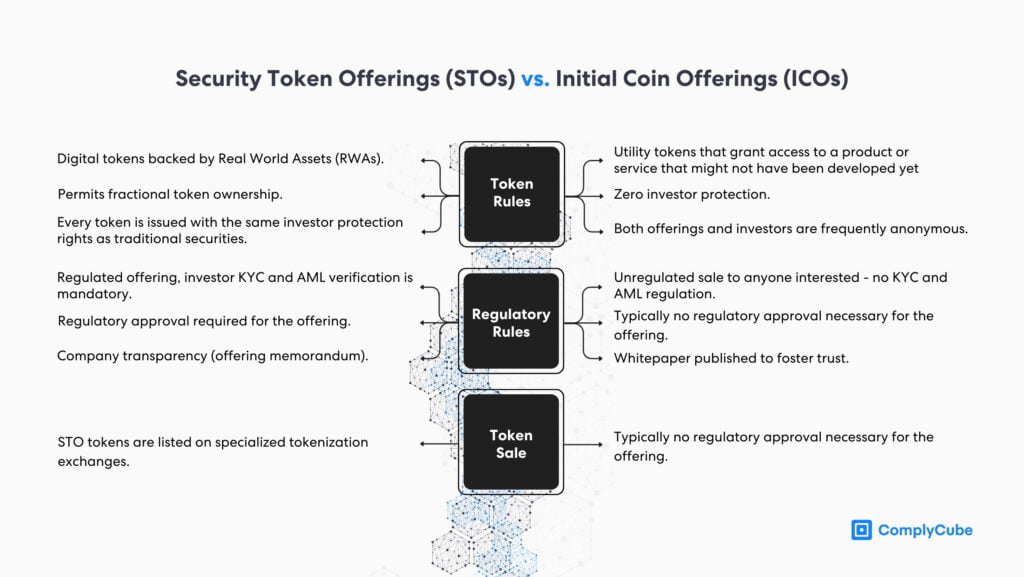
The Financial Action Task Force (FATF) regulates ICOs as any other Virtual Asset Service Provider (VASP). This means that all ICOs must adhere to the same AML and KYC regulations as Recommendation 15.
In the UK, however, the Financial Conduct Authority (FCA) has not produced clear guidance on how an Initial Coin Offering should be regulated, and as such, many are regulated on a case-by-case basis.
But we may ask you to explain why you think your activities are not in scope.
This is what an FCA flow chart states about firms operating a crypto business that do not arrange payment services, operate a payment machine, or provide custodian services. The UK is expected to reduce the ambiguity surrounding crypto businesses and related legislation in 2024, which should lead to further growth in the UK’s sector.
RWA Rules and Regulations
Tokenized Real World Assets and digital securities are liable to the same traditional securities laws as regular assets. In America, for example, the traditional securities markets are regulated by the SEC, which creates and upholds regulations designed to protect consumers of financial instruments (investors). Tokenized RWA exchanges must also receive a license by the same federal regulator.
Security Token Offering Regulations
STOs and digital securities must adhere to the same traditional securities laws as regular securities. These include:
- Registration: Issuers of digital securities must still register their equity tokens with the necessary regulatory body, the SEC in America, for example.
- Disclosure: All necessary information about the securities and issuers must be provided for investor transparency.
- Reporting: Company reporting obligations must be met, such as financial statements, investor relations updates and related business developments.
Issuers and intermediaries must then adhere to a suite of AML and KYC regulations. This involves the thorough identification and vetting, known as Customer Due Diligence (CDD), of users who wish to trade or invest in securities. For more information about the CDD process, What is Customer Due Diligence?
The same regulations must also be adhered to by broker-dealers. However, these institutions must gain a particular license to provide their services. The regulations they adhere to go beyond the verification of customers, the storage of transaction data, and customer interactions are pivotal.
There is also a matter of verifying that the individual has the right to purchase of invest in the securities, known as accredited investor verification. Such an example would be private placements (non-public offerings, typically to individuals or groups that provide a company with more than just financial funding).
Blockchain-Specific Securities Regulations
Due to digital securities being listed, transferred, and stored via a Distributed Ledger Technology (DLT), the protocols that facilitate digital securities trading, such as INX, must receive smart contract audits for security.
A code audit is typically conducted to search for vulnerabilities that a hacker could exploit to drain the treasury, liquidity pools, or other digital zones where funds are stored. The tokenization platform must also take measures to ensure that operations can be conducted securely on a day-to-day basis.
It is heavily suggested that exchanges like this conduct rigorous Identity Verification (IDV) steps to ensure that their users are who they say they are. These are the same typical checks that most regulated Centralized Exchanges (CEXs) conduct when a new user signs up.
A typical AML and KYC flow would consist of the following steps:
- Document verification
- Biometric (selfie) verification
- Address verification (where applicable)
- Background CDD checks
- Continuous monitoring
Following an adequate appraisal of the potential risk a new user might pose, their transactions are screened and monitored where necessary to ensure that any suspicious behavior is identified, tracked, and remedied as quickly as possible. For more information about crypto compliance, read How KYC Crypto Regulations Safeguard the Industry.
ComplyCube’s STO Compliance Solutions
ComplyCube boasts a comprehensive suite of AML and KYC solutions that are used in multiple industries across the world. In the blockchain and trading sectors, they have helped companies expand to 220+ regions compliantly while onboarding new customers in under 30 seconds.

Such a capacity to sign new customers up quickly is fundamental in the digital assets space and has been a growth catalyst for many firms around the world. However, their AML solutions go beyond client acquisition strategies.
The industry leader supplies a range of AML services, such as:
- Adverse media checks
- Sanctions and PEP screening (Politically Exposed Person screening)
- Watchlist Screening
- Transaction screening and monitoring (available via a partner’s API solution)
All of these AML solutions are available 24/7, ensuring that ComplyCube clients are fully protected from malicious activity, whatever form it might take.
Reach Out to an STO Regulatory Expert Today
If your STO, crypto, or fintech platform requires an optimized Identity Verification, Know Your Customer, or Anti-Money Laundering strategy, reach out to a ComplyCube specialist today to learn how they can help.