TL;DR: Counter-Terrorist Financing (CTF) refers to the regulations, controls, and technologies used to prevent the funding of terrorism. Terrorist groups exploit cash economies and front companies to obscure fund flows. This guide explains how businesses can mitigate CTF risks using advanced screening, identity verification, and real-time compliance automation.
What is Counter Terrorist Financing?
Counter-Terrorist Financing (CTF) is a cornerstone of global security and compliance. Terrorist organizations depend on a steady flow of money to operate. Stopping terrorist financing is one of the most effective ways to disrupt extremist organizations. While individual attacks may be cheap to carry out, the wider networks behind them need constant funding.
This money helps recruit additional members, spread propaganda at scale, maintain safe houses and logistical networks. Additionally, financing helps with the acquiring of weapons and equipment, as well as fund international travel and other operational expenses. Without this steady flow of financial support, extremist groups often struggle to coordinate, resource, and execute their plans, which significantly reduces their capacity to prepare for and carry out attacks.
Why Counter-Terrorist Financing Matters
Terrorist financing is harder to detect than other forms of financial crime. Financiers draw funds from both legal and illegal sources. They often divert donations, charities, and personal savings alongside proceeds from drug trafficking, extortion, or corruption. This blending of legitimate and illicit funds makes transactions appear routine even when they are not.
Past cases show the dangers of overlooking these networks. For example, the 9/11 Commission Report revealed that al-Qaeda raised and moved millions. They did this through front companies, charities, and informal transfer systems. Many of these transfers were small and routine, yet together they supported one of the most devastating attacks in history.
To reduce these risks, governments and regulators have developed strict CTF frameworks. These require financial institutions to verify customer identities, monitor transactions, file Suspicious Activity Reports (SARs), and screen clients against sanctions and watchlists. Such measures are not only regulatory obligations but also vital safeguards for public safety and the stability of the global financial system.
How do terrorists evade CTF measures?
In order to evade counter terrorist financing measures, financiers use a mix of both traditional and modern techniques to obscure money flows. Even still, cash remains the most common method, particularly in regions with weak oversight. This is because cash transactions leave zero trail. They allow funds to move very quickly without alerting regulators for further inspection.
New digital channels have made detection even harder. Online payment services, prepaid cards, and cryptocurrencies enable cross-border transfers that are fast and often anonymous. Terrorist groups find cryptocurrencies especially attractive, as they can layer funds through multiple wallets and exchanges before moving them to a final destination.
Informal value transfer systems also remain popular. These networks operate on personal trust rather than formal contracts. Since settlements happen outside regulated banking systems, transactions leave no official record, making them almost invisible to authorities. Global watchdogs highlight the scale of the challenge. The United Nations has stressed that it is difficult to measure the success of counter-terrorist financing against terrorist financing because much of the activity is hidden.
Countries around the world must use the intelligence in this report to build a stronger picture of the threats they face
According to the Financial Action Task Force (FATF) Comprehensive Update on Terrorist Financing Risks (July 2025), terrorist groups are adapting quickly to exploit financial loopholes. President Elisa de Anda Madrazo warned: “This continued abuse of the financial system poses a serious threat to global security and undermines international peace. Countries around the world must use the intelligence in this report to build a stronger picture of the threats they face and harness the tools available through the FATF Global Network to strengthen international cooperation and intelligence sharing.”
How do terrorist organizations secure funding?
Terrorist organisations and their sympathizers rely on multiple funding streams, combining both legal and illegal sources. Some notable schemes include:
- Drug trafficking is one of the most lucrative sources of revenue. Groups such as the Revolutionary Armed Forces of Colombia (FARC) financed their operations for decades through cocaine production and distribution. Proceeds were laundered across international networks before reaching militant leaders.
- Front companies provide another channel. These businesses appear legitimate but are often used to move or disguise illicit funds. Historical accounts suggest Osama bin Laden operated a honey business to transfer money and goods across the Middle East while avoiding scrutiny.
- Charities and non-profit organisations have also been exploited. However, while most operate with genuine humanitarian objectives, some have been misused to divert donations into extremist causes. This misuse undermines trust in the sector and complicates regulatory oversight.
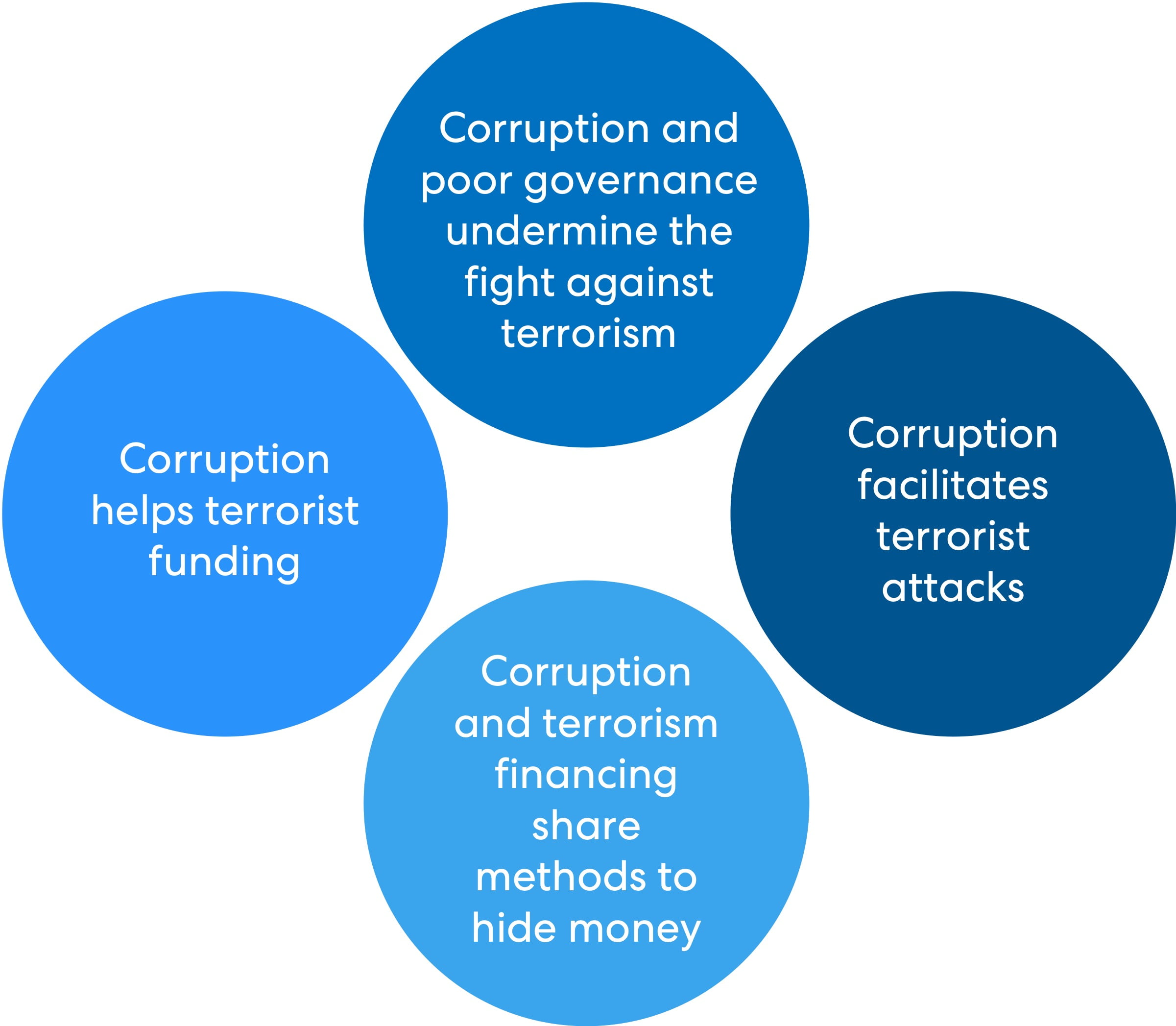
- Corruption and bribery are key enablers of terrorist financing, particularly in fragile or unstable states. Officials who accept payments or ignore suspicious activities allow terrorist funds to flow unchecked. This not only strengthens terrorist groups but also weakens governance and the broader fight against extremism.
- Cybercrime has emerged as a growing source of revenue. Extremist groups are increasingly using phishing schemes, ransomware, and fraudulent online fundraising to generate income. These methods allow funds to move quickly across borders with limited traceability.
According to Europol’s EU Terrorism Situation and Trend Report (TE-SAT 2024), extremist groups are diversifying their funding methods by combining criminal activities with legitimate-looking financial flows.
The variety of funding sources highlights why Counter-Terrorist Financing (CTF) is so challenging. In particular, from narcotics and cybercrime to corruption and charities, terrorist groups exploit every possible channel. For regulators, financial institutions, and law enforcement, this means vigilance must extend far beyond traditional money-laundering models.
Case Study: How ETA Used Extortion for Terrorist Financing
UK-linked facilitation suspected of supporting Babbar Khalsa
HM Treasury said it had reasonable grounds to suspect that Gurpreet Singh Rehal supported organisations linked to terrorism in India, including by promoting and encouraging activity, recruiting, providing financial services, and assisting networks connected to Babbar Khalsa (Babbar Khalsa International), including support involving weapons.
Domestic Counter-Terrorism sanctions to cut off access to funds
On 4 December 2025, HM Treasury imposed an asset freeze and director disqualification on Gurpreet Singh Rehal, and imposed an asset freeze on Babbar Akali Lehar, under the Counter-Terrorism (Sanctions) (EU Exit) Regulations 2019 and the “Counter-Terrorism (Domestic)” regime.
Asset freezes + bans designed to choke off funding and prevent enablement
- The UK froze all UK-based funds and economic resources that Rehal and Babbar Akali Lehar owned, held, or controlled, and barred UK persons and firms from dealing with them or providing funds/financial services (unless licensed or exempt).
- The UK disqualified Rehal as a director, stopping him from acting as a company director or taking part in company management in the UK.
- HM Treasury extended the measures to entities it said Rehal owned or controlled, including Saving Punjab CIC, WhiteHawk Consultations Ltd, and Loha Designs.
- HM Treasury framed the action as the first use of the Domestic Counter-Terrorism regime to disrupt funding linked to Babbar Khalsa.
- The government warned that breaches can trigger criminal penalties (up to 7 years’ imprisonment) and/or significant civil penalties.
How the world is fighting Terrorist Financing?
Counter-Terrorist Financing (CTF) rests on international conventions, regional frameworks, and national laws. Together, they close loopholes, harmonise standards, and give regulators the tools to disrupt illicit financial flows.
International standards
The UN International Convention for the Suppression of the Financing of Terrorism (1999) requires states to criminalise terrorist financing and cooperate in investigations and prosecutions. The FATF 40 Recommendations set the global benchmark for Counter-Terrorist Financing and Anti-Money Laundering measures. In February 2025, FATF strengthened obligations on digital onboarding and virtual assets. Its Comprehensive Update on Terrorist Financing Risks (July 2025) reported that many jurisdictions still face significant enforcement gaps.
Regional cooperation
The African Union has established a continental legal base. In addition, the OAU/AU Convention require member states to criminalise terrorist financing and strengthen judicial and border cooperation. The African Model Law on Counter Terrorism (2011) offers a template for asset freezing, information sharing, and investigation. Capacity building is supported through the AU’s ACSRT.
In 2024, the European Union introduced a new regulation and directive that harmonize AML and CTF obligations and created the Anti-Money Laundering Authority (AMLA), which will begin operations in 2025. For situational awareness and emerging typologies, see Europol’s EU Terrorism Situation and Trend Report (TE-SAT).
National frameworks
- United States: The USA PATRIOT Act (2001) and the Bank Secrecy Act require enhanced due diligence, suspicious activity reporting, and asset freezing where appropriate.
- United Kingdom: The Proceeds of Crime Act 2002 enables seizure and recovery of terrorist-linked assets. UK competent authorities updates The Money Laundering, Terrorist Financing and Transfer of Funds Regulations 2017 periodically to reflect FATF standards and technological change, including guidance on digital identity.
- United Arab Emirates: The core framework is Federal Decree-Law No. 20 of 2018 on AML and CFT. Following FATF grey-listing in 2022, the UAE strengthened supervision of high-risk sectors and increased penalties for non-compliance.
- Singapore: CTF obligations are set out in the Terrorism (Suppression of Financing) Act and the Corruption, Drug Trafficking and Other Serious Crimes (Confiscation of Benefits) Act. The Monetary Authority of Singapore issues binding AML and CFT notices for banks and payment firms, including oversight of virtual asset providers. See MAS Notices.
- Australia: AUSTRAC enforces the Anti-Money Laundering and Counter-Terrorism Financing Act 2006, which underpins CTF supervision, risk assessments, and intelligence sharing with regional partners.
These frameworks show growing convergence in CTF enforcement. FATF sets the baseline. Regional organisations such as the African Union and the European Union strengthen cooperation. National regulators adapt rules to local risks. Compliance teams must align with global standards and pay close attention to jurisdiction-specific obligations, especially for digital identity, sanctions screening, and virtual assets.
What’s the Difference Between CTF and CFT?
The terms Counter-Terrorist Financing (CTF) and Combating the Financing of Terrorism (CFT) both describe the global effort to identify, disrupt, and prevent the flow of funds that support terrorism. The difference lies mainly in how and where the acronyms are used. CTF is the preferred term in the world of financial services, compliance, and regulation. Banks, fintechs, and payment providers use it when discussing obligations such as Customer Due Diligence (CDD), Know Your Customer (KYC) checks, sanctions screening, and the filing of Suspicious Activity Reports (SARs). For example, the UK’s Money Laundering, Terrorist Financing and Transfer of Funds Regulations (2017, amended 2025) refer specifically to CTF when outlining business responsibilities. d
CFT is more common in treaties, conventions, and intergovernmental discussions. The United Nations’ International Convention for the Suppression of the Financing of Terrorism (1999) consistently uses the term CFT, as does the Financial Action Task Force (FATF) in its recommendations and risk assessments. Within the European Union, references often appear in the combined form “AML/CFT,” such as in the EU AML/CTF Package (2024), which harmonises rules for banks, fintechs, and virtual asset providers.
Although the two acronyms come from different traditions, they mean the same thing in practice. Whether a regulation refers to CTF or CFT, the obligations remain identical: to stop terrorist groups from raiansing and moving funds. For compliance teams, the distinction is largely semantic, but recognising both terms ensures clarity when engaging with regulators and international partners.
Key Takeaways
- Terrorist financing relies on informal networks, front companies, and illegal trade.
- FATF and other global framworks drive enforcement against terrorism funding.
- Corruption, crypto, and decentralized channels are common tactics.
- Adequate tools need to be implemented for identity checks and transaction screening.
- ComplyCube’s AI-powered compliance tools help businesses detect CTF risks and stay aligned with evolving regulations.
How Terrorist Financing is Prevented in Practice
Preventing terrorist financing relies on a layered approach that blends regulation, technology, and intelligence sharing. The first step is Customer Due Diligence (CDD) and Know Your Customer (KYC) checks. These confirm the identity of clients, assess risk, and ensure that businesses are not onboarding individuals or entities connected to terrorism. Where higher risks are identified, firms must apply Enhanced Due Diligence (EDD), including deeper background checks and closer scrutiny of activity.
Ongoing risk-based monitoring is equally important. Rather than focusing only on individual transactions, this approach continuously reviews customer behaviour, account activity, and exposure to high-risk jurisdictions. It ensures that risk assessments remain dynamic and proportionate, adjusting to changes in customer profiles and global threat patterns. When suspicious activity is detected, firms must file Suspicious Activity Reports (SARs) with their national financial intelligence units.
Sanctions and watchlist screening is another example of a safeguard. Customers must be checked against customers and transactions against global databases of designated terrorists, organizations and politically exposed persons. Failure to comply with sanctions requirements can result in significant penalties and reputational damage.
To manage obligations at scale, modern compliance teams rely on technology. ComplyCube supports these requirements by combining identity verification, sanctions and PEP screening, and adverse media checks with continuous monitoring. Its AI-powered engine reduces false positives, flags high-risk cases, and ensures compliance teams meet regulatory requirements across multiple jurisdictions. Biometric verification and liveness detection add further protection against impersonation and identity fraud.
With ComplyCube, institutions can reduce manual workload, minimise false positives, and focus resources on genuine risks.
By combining regulatory obligations with advanced automation, financial institutions can build a multi-layered defence while strengthening global counter-terrorist financing efforts by reducing the ability of terrorist groups to raise, move, and use funds.

Frequently Asked Questions
What is the difference between Anti-Money Laundering (AML) and Counter-Terrorist Financing (CTF)?
Anti-Money Laundering (AML) refers to measures designed to stop criminals from disguising the origins of illicit funds. Counter-Terrorist Financing (CTF) focuses specifically on preventing money from being raised, moved, or used to support terrorism, even if the funds come from legal sources.
What are common methods of terrorist financing?
Terrorist groups use a mix of legal and illegal methods. These include drug trafficking, front companies, charities, corruption, and cybercrime. Increasingly, digital assets and informal value transfer systems such as hawala are also being exploited.
Who regulates counter terrorist financing globally?
The Financial Action Task Force (FATF) sets the global standard for Anti-Money Laundering and counter-terrorist financing measures. At a regional and national level, regulators such as AUSTRAC in Australia, the Monetary Authority of Singapore (MAS), the UK’s Financial Conduct Authority (FCA), and the U.S. Financial Crimes Enforcement Network (FinCEN) implement and enforce these rules for counter-terrorist financing.
Why is sanctions screening important in counter-terrorist financing?
Sanctions screening ensures that individuals, organisations, and jurisdictions linked to terrorism cannot access financial services. Breaching sanctions can lead to heavy fines, reputational damage, and even criminal liability for financial institutions.
What is the difference between CTF and CFT?
There is no substantive difference. CTF is more commonly used in compliance and regulatory settings, while CFT appears more often in treaties and international law. Both terms describe the same goal of stopping terrorist groups from accessing and moving funds.