TL;DR: NFC ID supports identity verification by enabling document verification through WiFi-free, short-range chip reading on ePassports/ID cards. If you’re asking what is nfc is, it’s the near-field connection that uses BAC/PACE to access the chip, then runs cryptographic checks. NFC ID verification can also add biometric matching using the chip’s high-quality portrait.
What is NFC Technology?
Near-field communication (NFC) is a type of identity verification used to wirelessly connect devices over short distances. NFC is conducted over a range of no more than a couple of inches. It also enables seamless data transfer to the highest available precision. In ID verification, this lets an NFC-enabled phone read data directly from the chip in an ePassport or ID card in seconds.
If readers are unfamiliar with the name, they will know the concept. NFC technology powers everyday transactions such as Apple Pay, Google Pay, contactless payment cards, and many other scanning events in multiple industries. The same “tap-and-go” interaction is what makes NFC useful for fast, secure identity checks.
RFID Chips
Previously, Radio Frequency Identification (RFID) chips were the means through which wireless data was shared. This technology enabled information sharing and reading specifically via radio waves. These radio waves are transmitted via wave propagation and can travel without fading for extremely large distances.
NFC chips, however, use a different frequency of waves to create an environment for short-range data sharing. It transmits data via magnetic field induction, corresponding to a wavelength of 22 meters, with a frequency of 13.56MHz. This short-range behaviour is what makes NFC well suited to secure “tap-to-read” document checks.
Typically, NFC waves fade out far quicker than radio waves, making them far more secure. During an NFC data transfer, the proximity at which any device must be in of the event is a couple of inches, making attempts at data compromization futile.This close-range requirement also reduces the chance of interception in busy public spaces.
NFC technology strengthens security by using cryptography. It encrypts chip data, so only NFC-enabled devices can view it after they cryptographically verify the information. This encryption ensures that even if the data is intercepted, it remains unreadable without proper authentication.
How NFC ID Verification Works
Document verification is the verification of government-issued electronic identity documents, including biometric national identity cards such as passports and driver’s licenses. Modern verification methods use advanced verification systems to verify and validate client information through an uploaded image. This provides a baseline level of assurance before adding stronger verification methods.
NFC identity document verification adds an additional layer of security. This ensures secure data transfer for identity verification. From a document to an enabled device in seconds, NFC provides a frictionless onboarding process while maximizing security. It also helps organisations increase confidence in the document’s authenticity without adding extra steps for the user.
Data Extraction in NFC ID Verification
The NFC identity verification flow involves two processes. The processes are data extraction and cryptographic validation. Once a user places an NFC document near an enabled device, the 4-step NFC verification begins. This makes it easier to strengthen assurance while keeping the onboarding journey fast and intuitive.
Secure Data Access
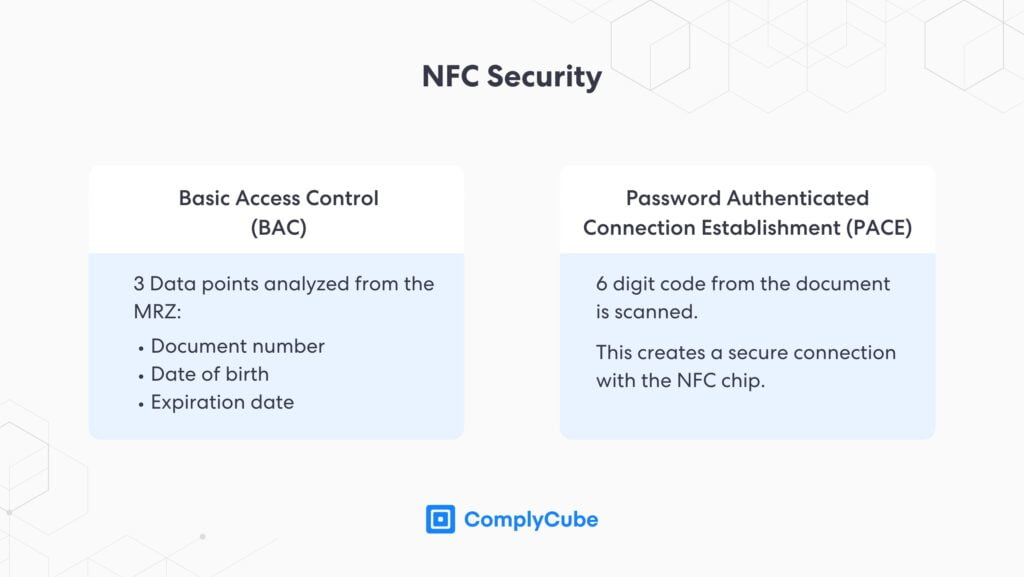
NFC verification typically starts in one of two ways: Basic Access Control (BAC) or Password Authenticated Connection Establishment (PACE). Both methods help establish a secure session before the device reads data from the chip.
- BAC verifies passports using three MRZ details: the document number, date of birth, and expiry date. The system combines these values to create a session key. It then uses that key to decrypt the NFC chip data and start secure identity verification.
- PACE works slightly differently for national ID cards. The user scans a 6-digit code from the front of the document. The system uses that code to create a secure connection to the NFC chip and begin processing.
Once the device establishes the connection, it reads and extracts data from the NFC chip, including the ID document details and a high-resolution biometric portrait, of the individual. The system can then use this chip-sourced data to support downstream verification checks.
Cryptographic Verification with NFC Technology
The verification process begins with passive authentication, ensuring the chip has not been tampered with since issuance. It cryptographically verifies each data element using the private key. This ensures the integrity of the data before proceeding with further checks.
Following this, the NFC chip undergoes active authentication, which sends the NFC chip a challenge-response test. Assuming the chip is genuine and not a replica, it will generate a response with its private key to verify its authenticity. This step adds an additional layer of security to confirm the chip’s legitimacy.
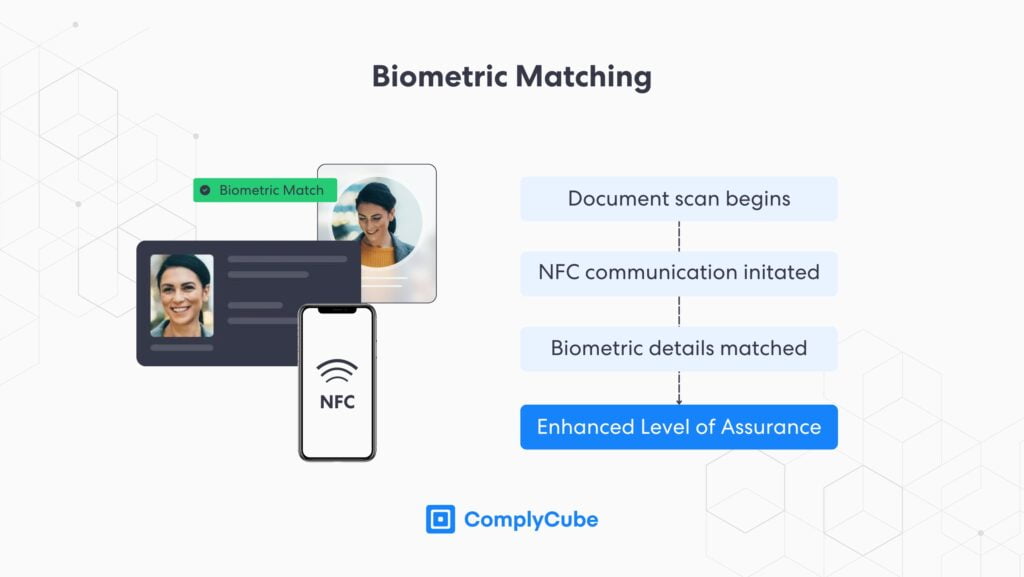
Biometric Matching
When a high Level of Assurance (LoA) is required, IDV must involve a biometric verification step. Biometric verification involves a user taking a live selfie or video for even stronger results, which is analyzed for liveness, and tampering along with many other compliance specifications. The supplied image or video is compared with the stock photo from the ID document for similarities. For more information on biometric verification, read the Advantages of Biometric Authentication.
NFC-based ID verification pulls a higher-quality stock image from the chip than a smartphone photo of the document. That gives the verification engine a clearer reference image. It can then compare faces more consistently and produce more reliable match results. This improves match confidence, especially when camera lighting or image sharpness varies.
Case Study: UKVI’s e-Visa expansion and NFC-based identity confirmation
Scale digital immigration while reducing reliance on documents
In late 2025, UK Visas and Immigration (UKVI) was accelerating its move away from physical documents and visa vignettes toward a digital record of identity and immigration status (an eVisa). UKVI positioned this as a phased transition to manage scale, while keeping the experience practical for applicants to need to prove status at the border and to third parties.
Expand eVisa coverage and use UK Immigration ID Check app
On 11 November 2025, UKVI confirmed the shift to eVisas, with physical evidence reduced—some routes moved from 30 October 2025, and some work/study applicants stopped receiving vignettes from 15 July 2025.
To support these digital journeys, the UK Immigration: ID Check app lets applicants prove identity online and set up eVisa access by scanning supported biometric documents via NFC, checking the document is genuine and belongs to the holder.
Clearer, more resilient applicant support
- From 30 Oct 2025, some approved applicants no longer receive a vignette and must use a UKVI account/eVisa.
- From 11 Nov 2025, UKVI invited more applicants to set up a UKVI account to access their eVisa.
- UKVI positioned eVisas as more secure than physical documents and faster for proving status (border, employers, landlords).
- From 1 Sep 2025, UKVI funded 25 community organisations (up to £400k, to 31 Mar 2026) to support vulnerable users.
Benefits of Using NFC ID Verification
An NFC verification process strengthens a company’s IDV tech stack without reducing the User Experience (UX). Enhancing the UX is a fundamental practice in modern-day client acquisition processes and is one of the leading factors behind customer churn. A faster, smoother onboarding flow can also reduce drop-offs during sign-up.
Frictionless UX
Near-field communication technology can transmit data in seconds between NFC-enabled biometric passports or ID cards and NFC-enabled smartphones. NFC-based verification allows new customers to sign up with contactless technology, contributing to an institution or company’s commitment to customer excellence.
A 2024 report found that the median churn rate in the financial services industry was 19%, a direct consequence of poor customer experience (UX). Traditional Financial Institutions (FIs) have been disrupted over the past few years primarily due to the gap in customer understanding. Neobanks have been leading this disruption.
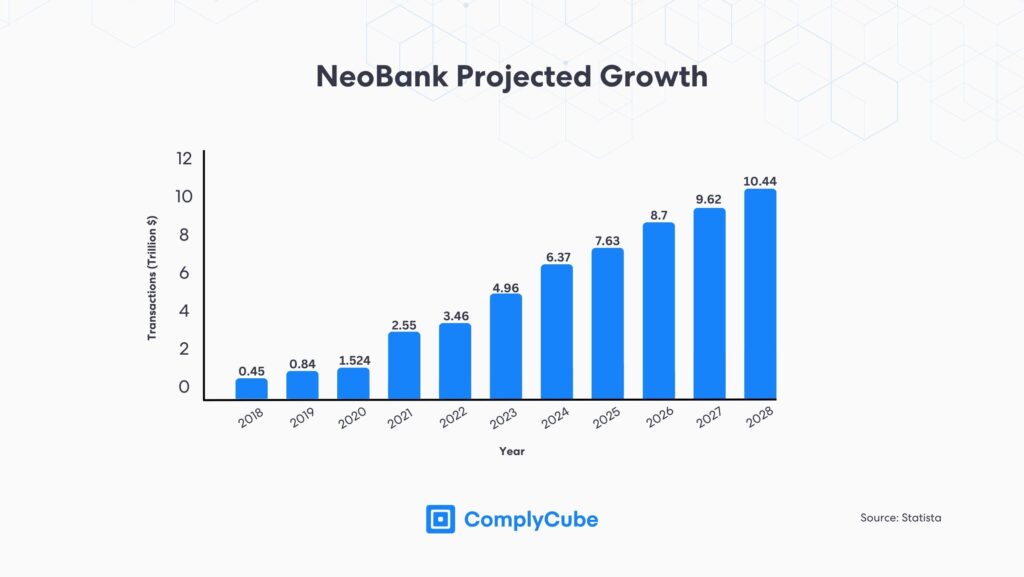
However, it is not only neobank but all modern financial services. This includes payment solutions and crypto exchanges, that now leverage sophisticated compliance solutions, such as NFC ID verification. The adoption of NFC and automated technology has allowed neobank and crypto exchanges to grow their user base astronomically over the past 5 years.
Deter Fraudsters
NFC verification makes it hard to forge documents that still pass an NFC reader. That directly reduces successful identity fraud attempts. The NFC chip protects biometric data and only allows decryption in specific cases. Fraudsters can’t easily copy or alter the chip and reuse it. This raises the effort and cost for bad actors. It also lowers the payoff for criminals who try to scale forgery.
NFC ID Security
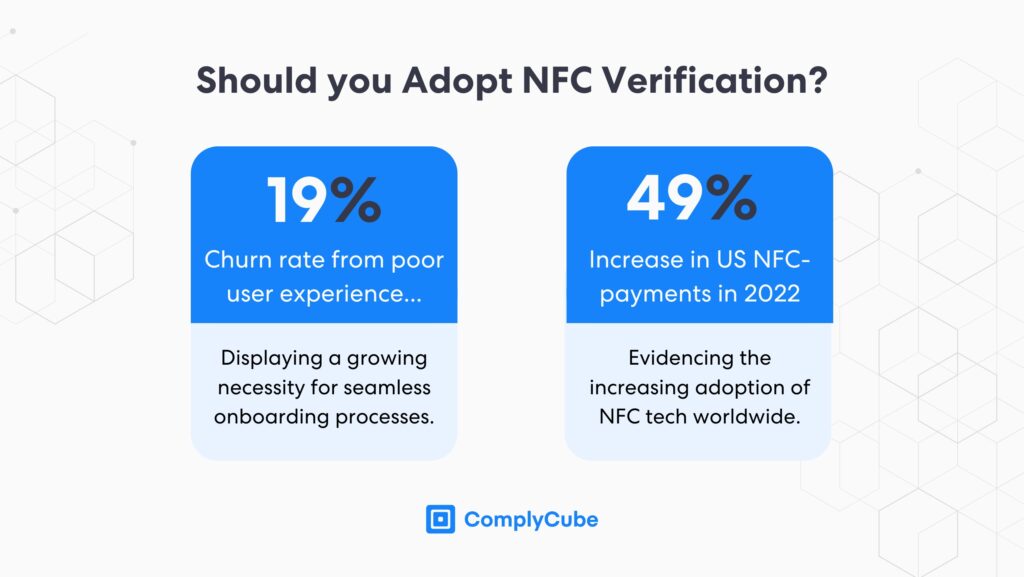
NFC verification protects identity documents by transferring data over a short, close-range connection instead of longer-range methods, which reduces interception risk and keeps the exchange secure end to end. This is why businesses have widely adopted NFC for contactless payments. In 2022, US mobile payments increased from 29% to 43.2%, displaying a growth of 49% in the sector.
American contactless mobile payments grew by 49% in 2022.
Compliance solutions should strengthen security without forcing businesses to trade off customer experience. Adopting NFC technology enables institutions to maximize security while prioritizing UX.
Key Takeaways about NFC ID
- NFC chip-reading upgrades document checks from “looks real” to “cryptographically proven.”
- BAC/PACE is the gatekeeper step that enables secure chip access (passport vs. national ID).
- Passive + active authentication helps detect tampering and cloned chips.
- Biometric matching is stronger when the portrait comes from the chip (higher quality) vs. a photo of the document.
- NFC can improve fraud resistance without sacrificing UX.
About ComplyCube
ComplyCube is an award-winning SaaS compliance platform. It provides solutions to empower FIs, crypto platforms, telecom firms, and many others with regulatory adherence. With an intuitive, all-in-one dashboard, firms can take total control over the IDV process. The platform does this by setting personalized risk scenarios according to their unique Risk-Based Approach (RBA).
ComplyCube provides a suite of Anti-Money Laundering (AML) and Know-Your-Customer (KYC) solutions. This is in addition to its IDV services, making it a one-stop shop for modern compliance. For further queries about NFC ID verification or AML solutions, start a conversation with a specialist today.
Frequently Asked Questions
What is NFC ID verification?
NFC ID verification is a method of identity verification that uses Near-Field Communication to read the encrypted chip inside ePassports and electronic ID cards. This enables secure data extraction plus cryptography validation of the document.
How is NFC different from RFID for identity verification?
RFID (Radio Frequency Identification) can work over much longer ranges via radio waves. NFC is designed for very short-range transfers (a few inches), which reduces interception risk and supports encrypted, device-verified reads for ID checks.
How can crypto businesses stay compliant with AML regulations?
BAC (Basic Access Control) typically uses MRZ (Machine Readable Zone) data (document number, DOB, expiry) to create a session key to unlock the chip, while PACE uses a card access code (often a 6-digit number) to establish a secure channel – common for national ID cards.
What is passive and active authentication in NFC document verification?
Passive authentication verifies chip data integrity (detects tampering since issuance), and active authentication adds a challenge-response test to help confirm the chip is genuine rather than a replica.
How does ComplyCube use NFC in identity verification?
ComplyCube can add NFC ID verification as an extra layer in the identity verification flow – using chip data extraction plus cryptographic checks, and supporting biometric matching using the higher-quality portrait retrieved from the NFC chip to strengthen confidence in the verified identity.